CCleaner Hack Shows Value of Knowing Your Environment
Piriform, makers of CCleaner, a popular PC cleaning application, released a security notification on Monday announcing that several versions of the software had been infected with malicious code. Although Piriform and parent company Avast Software originally believed they were able to stop the attack before it did any harm, Avast researchers have since discovered that the malware selectively targeted large tech and telecomm companies, delivering a sophisticated, second-stage payload. Reportedly, Cisco, Microsoft, Gmail, VMware, Akamai, Sony, and Samsung were among those targeted. The origin and scale of the attack are not currently known, but Avast places the number of affected systems “likely at least in the order of hundreds.”
In the wake of malware outbreaks, IT teams have the opportunity to assess whether the tools at their disposal are providing enough visibility into their environment. Greater visibility is one way for IT to quickly neutralize threats by getting at the source of the problem, which in this case would be whether any users had installed a compromised version of CCleaner.
Modern users are extremely resourceful. If their needs are not met by software provided by IT, most do not hesitate to download applications (particularly free ones) to fill the gaps in their software portfolio.
Even users following good security practices when selecting and installing new applications could have been vulnerable to the CCleaner attack. According to Piriform’s website, CCleaner has been downloaded over 2 billion times with over 5 million desktop installs per week. Despite being a well-known and widely-trusted app, CCleaner was still an open target.
Not to mention that the incident unfolded under the nose of cybersecurity company Avast Software, which had acquired Piriform back in July. Avast clarified on Tuesday that they “strongly suspect” that Piriform was compromised prior to Avast’s acquisition.
The version of CCleaner containing the malware was released on August 15th and was first detected four weeks later by Morphisec, another cybersecurity company. Avast estimates that 2.27 million users were affected by the attack, with 730,000 users still running the affected version.
CCleaner’s trusted reputation and wide reach likely made it an attractive target for hackers. Cisco Talos, the cybersecurity team at Cisco, who followed the CCleaner attack, stated in a blog post that, “[f]or a period of time, the legitimate signed version of CCleaner 5.33 being distributed by Avast also contained a multi-stage malware payload that rode on top of the installation of CCleaner.” This kind of infiltration is known as a supply-chain attack, which Talos describes as “a very effective way to distribute malicious software into target organizations.”
As reported by Wired, supply-chain hacks have increasingly become a problem, with two similar attacks happening within the past several months.
How Should IT Address CCleaner or Other Supply-Chain Attacks?
We’ve recently discussed how IT can use intelligent analytics tools to protect users from WannaCry ransomware and identify users with unsupported hardware. Utilizing data collection and analysis tools is by far the fastest and most accurate route to understanding what hardware and software exists in your environment.
Lakeside’s workspace analytics solution, SysTrack, simplifies data discovery and is an ideal tool for identifying whether a given app has been downloaded on any of your users’ systems.
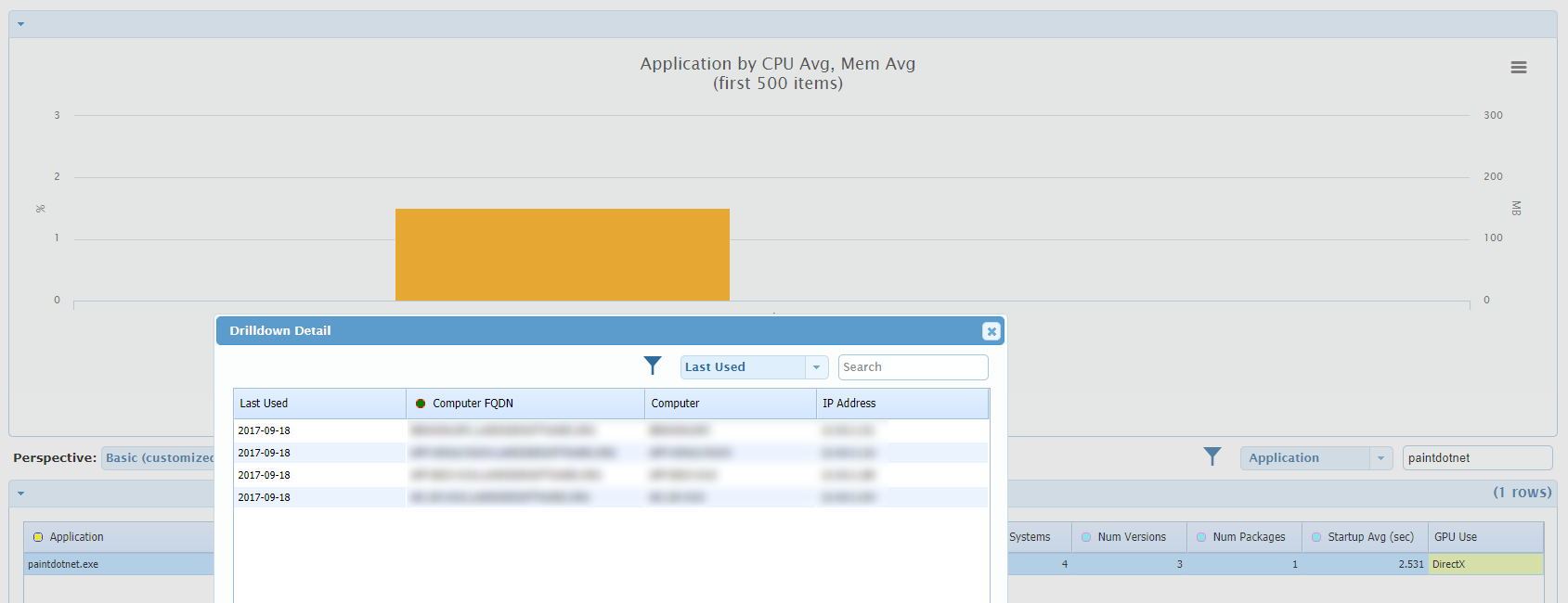
To provide a more illustrative view (no one in our demo environment has CCleaner installed), I used SysTrack to search for Paint.NET, another popular free app.
SysTrack identified four systems with Paint.NET installed. By drilling in, I was able to identify the exact users that had the app as well as how recently it had been used.
This view also shows me that three different versions of the software exist in my environment. By drilling into versions, I can see the exact version numbers that my users have installed.
In the case of a compromised app like CCleaner, IT can use SysTrack to search for software and versions of interest to quickly identify whether any of their systems may be at risk. SysTrack also allows IT to see how the app has been behaving, which could be useful in tracing any suspicious activity.
A second option for reducing the potential damage of a malware attack is to restrict which users have local admin rights on their machines. Without admin privileges, users are unable to self-provision apps in the first place.
Inevitably, exceptions will be made to who is allowed local admin privileges. Rather than respond to a user’s every request to install a new app, IT may extend privileges depending on organizational practices. While this is not an inherently bad practice, it is useful to keep track of which users have local admin privileges.
SysTrack provides customizable, easy-to-use dashboards like the one below that report on data of interest. In this case, IT can view the dashboard to identify users with local admin privileges and restrict as necessary to prevent undue risk in their environment.
As malware moves further up the supply chain, IT teams will have to adapt their security strategies. Workspace analytics solutions that collect, analyze, and store data on a wide variety of system characteristics provide IT with the visibility needed to inform decisions affecting end users. This level of visibility can help IT act quickly when malware is discovered to identify potentially-affected software in the environment and mitigate risk.
Increase Visibility with Workspace Analytics for IT
[Updated 9/22/17 to reflect discovered impact of second-stage malware payload and developing security investigation]
Subscribe to Lakeside Updates
Receive product updates, DEX news, and more



