
Care about digital employee experience? Here’s why you should think twice before deploying kernel mode agents.
In the aftermath of the recent cyberattack on SolarWinds — which The New York Times called “the most sophisticated hacking of government and corporations in history” — there is heightened focus on evaluating the risk profiles of IT monitoring tools.
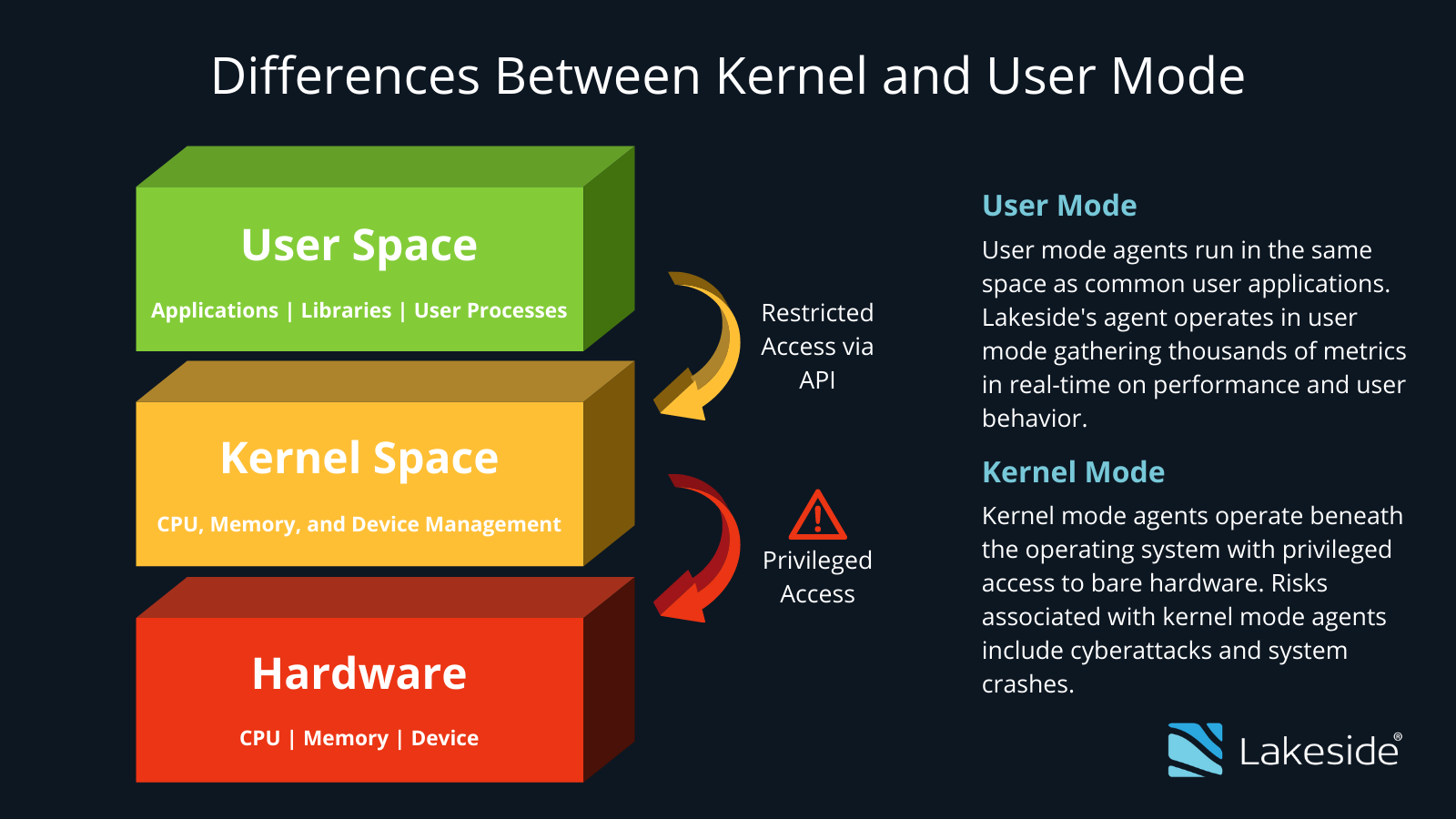
This scrutiny has resurfaced a longstanding debate around kernel mode vs user mode monitoring agents. While user mode agents have the same privileges as other common applications, kernel mode agents have access to the heart of a system, giving malicious actors free rein during an exploit.
Part of what makes the SolarWinds attack so catastrophic is the legacy kernel architecture of its Orion agent. Because SolarWinds’ agent runs in kernel mode, it’s fairly easy for malicious actors to use it to do illicit activities without being detected because it’s acting as the kernel. Once the attackers gained global access privileges, they were able to fly under the radar for over a year, stealing data from at least nine US government agencies and 100 private companies.
And the damage is far from over. Although organizations will have applied the security patch released by SolarWinds to address the vulnerability, this solution only addresses new exploits. Meaning that the attackers who have already found their way in with root access privileges likely remain there undetected.
For those wanting to guard against similar exploits in the future, the least risky option is clear: Don’t use IT monitoring software that requires kernel access. Instead, look for software with architecture that doesn’t rely on legacy on-prem models within today’s cloud-first, highly distributed digital workplace.
But the debate doesn’t end there. A second (and, in our eyes, equally compelling) reason exists to run away from kernel mode agents.
Kernel Mode’s Digital Experience Disruptions
The same flaw that led to the severity of the SolarWinds attack also has implications when it comes to digital employee experience (DEX). Because kernel mode technology has root system access, it interacts directly with users’ hardware which can cause the ultimate experience disruptor: blue screens of death (BSOD).
As an example, one of our competitors whose agent uses kernel mode components was the culprit of so many BSOD among their customers that they had to build a feature called “CrashGuard.”
Not only do BSOD eat into users’ time, but they can also cause the loss of unsaved work and potentially render the system useless, which can require IT intervention up to reinstalling the OS.
Apart from system crashes, components running in kernel mode degrade experience in more insidious ways. Kernel mode activity is accounted for as part of the OS, so any resource consumption gets attributed to kernel mode threads. Just as privileged access makes security exploits much harder to detect, kernel mode resource consumption isn’t visible as any process because it’s treated as part of the OS. So if you have an agent with kernel mode drivers, you may be chewing up a lot of resource and slowing the system down but nobody can see it.
Why Lakeside’s DEM Solution Operates in User Mode
At Lakeside Software, we believe that your digital experience management (DEM) solution should never be the reason DEX is deteriorating. Our software does not operate in kernel mode, which makes our agent very safe to use in enterprise and government environments.
Some of the ways our agent differs from the competition include:
- User mode architecture: The SysTrack agent has been recognized by independent industry analysts as collecting the greatest breadth and depth of telemetry in the DEM space and it does so in a user mode context, providing a security advantage without sacrificing functionality.
- Lightweight design: The agent requires <1% of a system’s CPU and 40-60 MB of memory. Due to its user mode design, the SysTrack agent cannot cause BSOD. It is also easy to track how much resource the agent is requiring by monitoring the service.
- Multiplatform support: Our agent supports the broadest range of platforms, including Windows, MacOS, Linux, Chrome OS, and Android.
- Cloud-first: SysTrack is architected to scale easily to accommodate the largest enterprise environments whether on-prem or in the cloud. Our mature, multitenant cloud offering is designed to ensure that customer data is kept separate for optimal security and privacy.
Choosing the Best Digital Experience Management Solution for Your Environment
Platform security and performance are critical components of choosing your ideal DEM solution, but other factors such as use cases, integrations, and expected business value must also be evaluated. The following resources can help with your decision-making process:
- The Forrester New Wave for End-User Experience Management, Q4 2020: This report evaluates the top vendors in end-user experience management (EUEM) on 11 key criteria. It names Lakeside as a leader with differentiation in telemetry collection, qualitative feedback, third-party integrations, and roadmap criteria. You can download a complimentary copy of the report on our website.
- ROI of DEM calculator: This calculator evaluates the economic value of DEM across three key use cases: service desk improvements, asset optimizations, and productivity enhancements. It allows you to input information about your environment to increase the accuracy of the ROI estimate.
- Gartner Market Guide for Digital Experience Monitoring, 2020: Download a complimentary copy of this report to learn about the key concepts, use cases, and vendors within DEM.
- Free demo: Contact us to schedule a free product demo customized to your organization’s needs and use cases.
Subscribe to the Lakeside Newsletter
Receive platform tips, release updates, news and more



