
Among the many security threats companies currently face, at least one has caused widespread alarm in recent weeks.
New, critical security flaws in Apache Log4j 2 — a logging library widely used in millions of Java-based applications — is putting organizations at risk when using trusted, open-source software. With the latest vulnerabilities, sometimes referred to as Log4Shell, reaching as high as 10.0 on the Common Vulnerability Scoring System (CVSS), this flaw opens the door for attackers to break into systems, steal personal data, and infect networks with malware and ransomware.
So what does this mean for your organization, and how can IT teams quickly and effectively track down and resolve all instances of Log4j vulnerability? Here’s what you need to know.
Why Is Log4j a Big Deal?
Despite being a known problem, many organizations still have Log4j vulnerabilities lurking within their infrastructures. That’s because many tools fall short in identifying more than just the active instances across the IT estate, leaving behind other ticking time bombs that could result in a major breach.
If ignored, organizations not only risk having a major data breach but also getting pulled into a lawsuit. The U.S. Federal Trade Commision recently announced it will continue to pursue legal action against companies that fail to address Log4j security issues, along with other known vulnerabilities. In the case of Equifax, for example, failure to correct a known security vulnerability that exposed the personal information of 147 customers resulted in a nearly $700 million global settlement in 2019 with the FTC, the Consumer Financial Protection Bureau, and all 50 states.
“The FTC intends to use its full legal authority to pursue companies that fail to take reasonable steps to protect consumer data from exposure as a result of Log4j, or similar known vulnerabilities in the future.”
FTC.govJan. 4, 2022
What’s Being Done to Fix the Issue?
Apache has since released patched files to address this vulnerability, but the challenge for organizations is to identify their exposure across their estate.
With solutions such as Lakeside’s Digital Experience Cloud, powered by SysTrack, IT teams can gain the visibility needed to quickly respond to this kind of security situation. The platform provides not only a way to identify the company’s exposure but also tools to help remediate issues quickly and securely.
How Can IT Detect This Vulnerability?
While it’s true that all security tools will be updated to find this vulnerability, speed is key — faster remediation means greater safety.
After all, the biggest risk isn’t in the first wave of exploits, which tend to include a small number of bad actors trying to figure out ways to breach networks — it’s when attackers finally discover and share that method with others. At that point, attackers are empowered, increasing the scale and number of attacks exponentially and escalating the risk to organizations that have not yet patched their vulnerabilities.
What Can Lakeside Do to Help?
Lakeside has created a solution kit that is free for our customers and can easily be activated within hours for both cloud and on-prem deployments. Because of the forensic level of data Lakeside collects directly from endpoints, we can immediately help our early adopters identify risks across the estate.
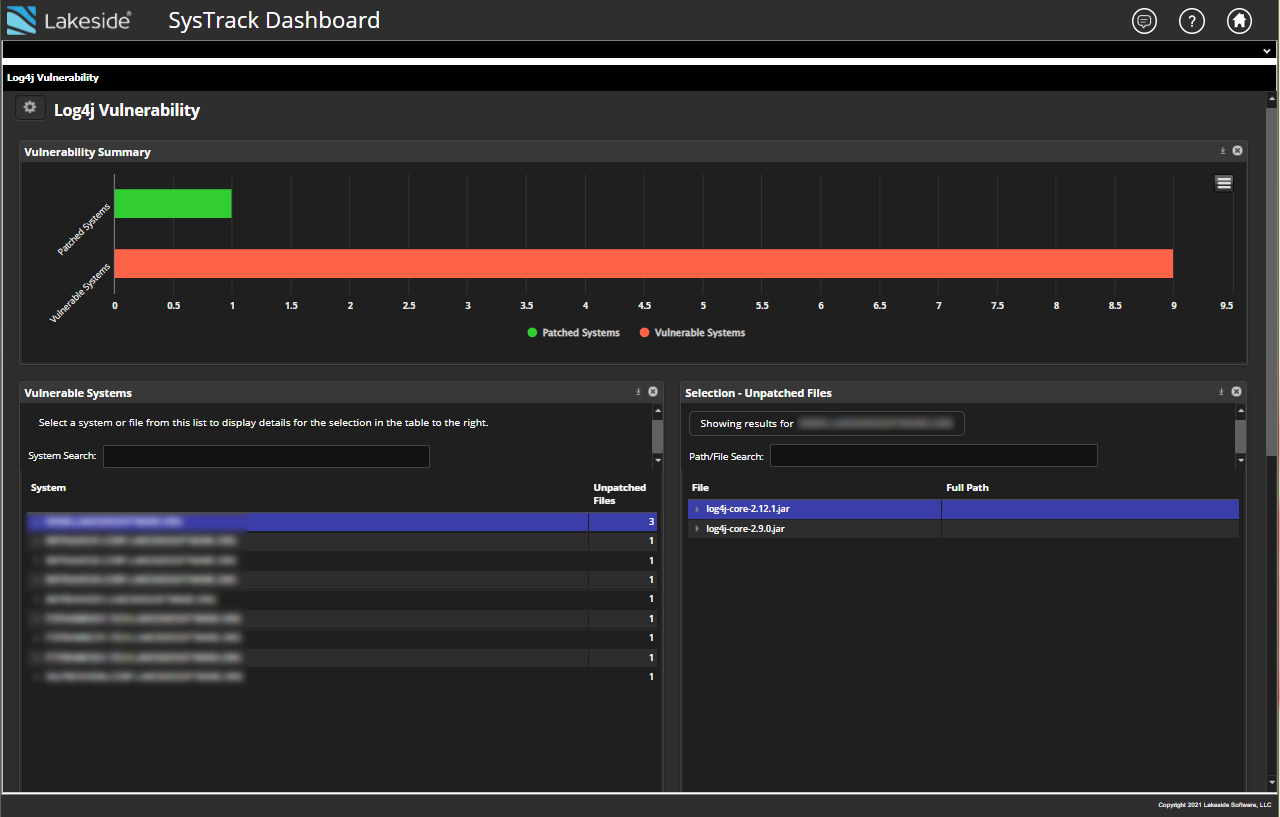
Once the Log4j solution kit has been imported and setup, IT can look for vulnerable devices across the IT estate using a customized dashboard.
Using Intelligent Edge architecture, Lakeside’s Digital Experience Cloud securely gathers relevant data on specific files or versions, allowing IT teams to identify any problematic instance of Log4j across the environment. With these insights, IT can prioritize remediation efforts for both active and inactive vulnerabilities.
Why Customers are Reducing Risk with Lakeside
Early adopter customers have found a substantial number of vulnerabilities that have gone undetected by leading information security tools. In one case, a customer found 988 vulnerable files across 64 different systems within an estate of 200 systems. These vulnerabilities were only found using Lakeside’s Digital Experience Cloud.
Subscribe to the Lakeside Newsletter
Receive platform tips, release updates, news and more



